ÍNDICE
Purposes pursued with the adoption of the obligations contained in this document
Personnel acting under the authority of the file manager
Consequences of non-compliance
For the personnel acting under the authority of the file manager
Procedure to file complaints or claims
Right of information and consent of the interested party
Special categories of personal data
RIGHTS OF THE INTERESTED PARTY
THE FILE MANAGER AND THE DATA CONTROLLER
OBLIGATIONS OF THE FILE MANAGER AND OF THE PERSONNEL UNDER THEIR AUTHORITY
The processing of personal data
USEFUL CONCEPTS
| TERM | DEFINITION |
|---|---|
| Personal data | Any information concerning identified or identifiable individuals. |
| Interested party | Natural person holder of the personal data. |
| File | Organized set of personal data, whatever the mode of creation, storage, organization or access. |
| Processing of data | Operations and technical procedures, automated or not, allowing for the collection, recording, conservation, elaboration, modification, blocking and cancellation, as well as the assignment of data resulting from communications, consultations and interconnections and transfers. |
| Automated processing | Processing performed through a device by means of an automatic system. |
| Non-automated handling | ESuch processing that is not automated. |
| Assignment of data | Any disclosure of data made to a person other than the interested party. |
| Consent of the interested party | Any manifestation of free, unequivocal, specific and informed will, by means of which the interested party consents to the processing of their data. |
| File manager | Natural or legal person deciding on the purpose, contents and use of the processing. |
| Data controller | The natural or legal person that, jointly or severally, processes personal data on behalf of the file manager. |
| Control body | Person or persons designated by the file manager to advise and supervise the processing of personal data. |
| Authorized access | Authorizations granted by the file manager to a user for data processing. |
| Access control | Mechanism that, based on the already authenticated identification, allows access to data or resources. |
| Authentication | Procedure for checking the identity of a user. |
| Password | Confidential information, often consisting of a string of characters, which must be used in the authentication of a user. |
| ID | Procedure for recognizing the identity of a user. |
| Security breach | Any breach of security causing the destruction, loss or accidental or unlawful alteration of personal data transmitted, preserved or otherwise processed, or the communication or unauthorized access to such data. |
| Information systems | Set of automated files, software, technological media and hardware used for storing and processing personal data. |
| Communications network | Infrastructure that allows for an information exchange to be maintained at a distance (voice, data, image or a mixture of the above). |
| Media | Physical object susceptible to be handled in an information system and over which data can be recorded or retrieved. |
| Resilience | Mechanism to recover its initial state when the disturbance to which it had been subjected has ceased. |
INTRODUCTION
Article 18 of the Spanish Constitution provides, in its first section, that the right to honor, personal and family privacy and to one’s own image is guaranteed. The General Data Protection Regulation was born, as indicated in Article 1, section 2, to protect the rights and fundamental freedoms of natural persons and, in particular, their right to the protection of personal data.
This Code of Conduct responds to this fundamental right and to the regulations developed by this principle and it has a legally binding nature for each and every one of the legal persons that make up the business group that will be detailed below, with the aim of contributing to the correct application of the data protection regulation.
The file manager acquires the obligation to approve this document by means of its administrative body.
Likewise, the file manager agrees to publish this document on its website, this is, asesorapericial.com.
The file manager undertakes to review and update this document manually and to notify the modifications to all personnel operating under its authority and those who have adhered to the code.
Within the review procedure, the file manager will place special emphasis on the evaluation of the effectiveness of this document in order to introduce improvements that result in greater effectiveness in the privacy policy adopted.
The file manager also undertakes to promote a culture of awareness based on the assumption of the principles of this document and the regulations in force.
The file manager is fully committed to cooperating with the data protection control authority that requests it and, in particular, with the Spanish Data Protection Agency.
If you have any doubt, suggestion, query, complaint or claim, please contact the Control Body.
Purposes pursued with the adoption of the obligations contained in this document
- Providing guarantees on the part of the file manager regarding compliance with data protection regulations.
- Providing a useful tool to the data controllers so that they offer guarantees of compliance with the data protection regulations by adhering to it.
- Providing publicity regarding the implication of the file manager with compliance with data protection regulations.
IDENTITY OF THE FILE MANAGER
ASESORA ASISTENCIA PERICIAL, S.L., an entity located in Madrid (28040), Plaza Ciudad de Viena 6, 2º, with Tax ID No. B85143832, is the file manager, legal person that determines the purposes and means of processing.
Identity of the Control Body
The Data Protection Security Manager is MS. ANA – MARÍA DELGADO LAVERDE, whom you can contact at the email address adelgado@asesorapericial.com.
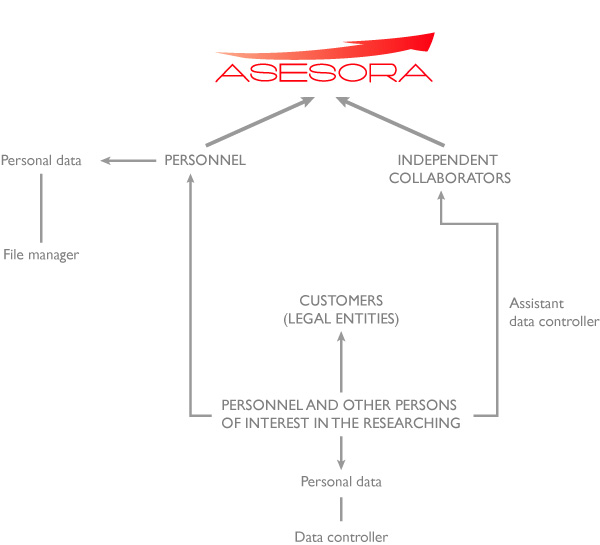
SET OF FILES
Accesses to the files are the following:
| FILE | DEPARTAMENTS | ||
| RESEARCH STAFF | ADMINISTRATION | EXTERNAL COLLABORATORS | |
| PERSONNEL | |||
| PERSONNEL AND OTHER PERSONS OF INTEREST IN INVESTIGATIONS (as the data controller) | Sub-manager of the processing | ||
The structured set of personal data subject to processing is the following:
| FILE | CATEGORIES OF DATA | SPECIAL DATA | PROCESSING | PURPOSE | LEGITIMATION | INTERESTED PARTIES | INTERNATIONAL TRANSFERS |
| PERSONNEL | Identification data
Personal characteristics Social circumstances Academic and professional data Job details Economic and financial data |
No | Mixed | Human Resources
Management of payroll |
Necessary processing for the execution of a contract in which the interested party is a contractual party
Consent of the interested party or their legal representative |
Employees
Job seekers |
Yes (Microsoft) |
OBJECTIVE SCOPE
This Code of Good Practices applies to the processing of personal data within the context of the activities of the file manager, regardless of where the processing itself or its modality (totally or partially automated or non-automated) is located.
SUBJECTIVE SCOPE
Personnel acting under the authority of the file manager
This code of conduct is of mandatory compliance for anyone acting under the authority of the file manager and having access to personal data. The file manager will convey the contents of this document by delivery in paper format.
Likewise, the file manager undertakes to inform the personnel on a regular basis regarding both the contents of this document and the European and national data protection regulations.
Any person acting under the authority of the file manager may ask for a copy of this document by requesting it to the Control Body.
In the event that a person acting under the authority of the file manager has a disability that prevents them from accessing the information in this document, the file manager agrees to make it accessible in such a way that the person can be aware of its contents.
Data controllers
Data controllers may adhere to this document and, therefore, be legally bound to its compliance, in order to ensure compliance with the obligations of Article 28 of the General Data Protection Regulations.
The procedure to adhere to this document consists of the legal bonding through the contract that regulates the processing by the data controller.
The file manager has a record of all those who carry out a data processing on their own, stating which of them have adhered to this document.
Consequences of non-compliance
For the personnel acting under the authority of the file manager
Failure to comply with this document by the personnel may lead to the opening of a disciplinary procedure.
In any case, as far as the disciplinary consequences are concerned, the provisions of the labor regulations in force will apply.
The file manager could in some cases implement eventual sanctions to the personnel responsible for the breach.
Some activities related to the improper handling of personal data may involve the commission of an offense with criminal consequences, such as the discovery and disclosure of secrets.
For the data controllers
In the event that a data controller fails to comply with this document if they adhered to it, the file manager may terminate the contract immediately, without any compensation in favor of the person in charge of the processing, regardless of the legal actions that the file manager can adopt.
Some activities related to an inappropriate processing of personal data may involve the commission of an offense with criminal consequences, such as the discovery and disclosure of secrets.
Procedure to file complaints or claims
In the event that someone is aware of the breach of this document or of the data protection regulations by a person bound to comply therewith, they may inform the Control Body via e-mail to protecciondedatos@asesorapericial.com
No anonymous complaint or claim will be answered.
The procedure to resolve the complaints or claims brought will be the following:
Anyone who wishes to file a complaint or claim must notify them to the email address stated above, clearly identifying their identity and the reason for their complaint or claim and providing all the evidence they deem appropriate.
The Control Body will have ten (10) calendar days to decide whether to admit the complaint or claim or not. Once this period has elapsed, the complaint or claim may be dismissed, which would be notified to the claiming party in an argued manner, or admitted, which would be notified both to the claiming and the contested party.
Save it is essential for its allegations, the contested party will not be notified of the claiming party’s identity (upon the decision of the Control Body).
The contested party will have ten (10) calendar days to present allegations, a period that may be extended, upon the argued request of the contested party and by a unilateral decision of the Control Body if the latter considers that the deadline was not sufficient.
Once this period has elapsed or the allegations of the contested party have been submitted, the Control Body will have thirty (30) calendar days to make a decision regarding the complaint or claim, under its sole and exclusive criterion, which will be communicated to both the complaining and the contested party.
The decision of the Control Body must always be argued in every case.
The decision of the Control Body cannot be appealed.
In the event that a person is not satisfied with a decision adopted by the Control Body, they may go to the Spanish Data Protection Agency to file a complaint or claim.
Sanctioning procedure
In any case, it will be based on the provisions of both the labor regulations and the data protection regulations.
GUIDING PRINCIPLES
It is essential to comply with these principles in the processing of personal data. The file manager is obliged by law to be able to demonstrate that it is duly complying with these principles, therefore the personnel processing the data will also be so.
Data lawfulness
The data will be processed in a lawful, loyal and transparent manner. To comply with this principle, save in case the file manager says otherwise, in order to proceed with the processing of personal data, the consent of the interested party must be obtained beforehand (vide “Guiding Principles” for the “Right to information and consent of the interested party“).
There are exceptions in which it is not necessary to have the consent of the interested party; you can consult them in “Guiding Principles“, the “Right to information and consent of the interested party” section.
Quality of the data
The data must be:
- Appropriate, relevant and limited to what is strictly necessary for the purpose pursued (Vide in “Security measures“, the “Minimization” section).
- They may not be used for purposes other than those for which they were collected (vide in “Guiding Principles” the “Principle of Legality of Data” section).
- There may be a need to process data for a purpose other than the one for which they were collected, but this can only be done if:
- The consent of the interested party is obtained again.
- The new purpose is closely related to the previous one.
- Personal data are anonymized.
In these and other cases, it is essential to consult with the Control Body.
- Accurate and updated. If they are found to be inaccurate, you must write it down and either replace them with the correct ones or cancel them (block them for later deletion).
- They will be stored in a way that allows for the exercise of the right of access readily.
- They will be canceled when they are no longer needed. They may be kept longer than necessary provided they are used exclusively for the purposes of filing in the public interest, for scientific or historical research purposes or statistical purposes (vide “Security measures” for “Pseudonymization“).
Safe treatment
The processing of data will guarantee their security at all times, particularly including measures preventing unauthorized or illegal processing, loss or destruction or accidental damage.
In the event that an unprecedented processing is going to be carried out, before the processing takes place the file manager will assess the impact of said processing on the rights and freedoms of the interested parties.
If you detect that this unprecedented processing situation is going to occur, contact the Control Body immediately to inform them.
Right of information and consent of the interested party
Information
No personal data may be used or requested without having informed the interested party first about the contents of the specific clause for each occasion.
What information should be provided whenever personal data are going to be processed?
| The identity and contact information of the file manager. |
| The purpose of the processing to which the personal data are destined and the legal basis of the processing. |
| The recipients or categories of recipients of the personal data. |
| International data transfers. |
| The term of conservation of the data or the criterion used to determine this term. |
| The existence of the right to request the data controller to exercise the rights of access, rectification, deletion, limitation of treatment, opposition and portability of the data. |
| When the legitimacy of the processing was the consent, the possibility of being able to withdraw it at any time. |
| The right to file a claim with a control authority. |
| If the purpose of the processing is to protect the legitimate interest of the file manager (Vide in “Guiding Principles” the “Consent“), indicate what is that legitimate interest. |
| If the treatment is based on a contractual relationship or a legal rule (Vide “Guiding Principles” for “Consent“). |
| If the interested party is obliged to provide the data and the possible consequence in case of not providing them. |
| If there are automated decisions, including the elaboration of profiles and, where appropriate, the logic applied, the importance and the consequences foreseen for the interested party. |
This information is provided to interested parties through the existing documentation for this. If you do not know how to access this documentation, contact the Control Body immediately.
Consent
The use of data can only be done in a lawful manner. This means that they must have the free, unequivocal, specific, express and reliable consent of the interested party, but there are exceptions to this obligation to request consent, which are:
- The use of data is necessary to execute a contract to which the interested party is a party. This would be the case, for example, of the employment relationship between the file manager / employee.
- The use is imposed or allowed by a legal rule.
- The use is necessary to protect the vital interests of the interested party or a third party.
- The use is necessary for the public interest.
- The use is necessary to protect legitimate interests of the file manager (provided that the rights of the interested party do not prevail). This could happen, for example, in the case the file manager had to defend itself against a possible claim.
The consent will be collected independently of any other communication or request, always in a clear and simple way, by means of the documentation that the file manager has for that purpose.
There is documentation for this and if you deem it necessary, you can request it to the Control Body.
When an individual provides personal data of a third party we also need the third party’s consent to be able to process their data
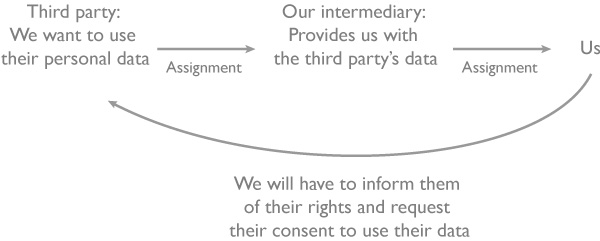
Remember that the interested party has the right to withdraw their consent at any time.
If you have any doubts about this, please contact the Control Body.
Special categories of personal data
The above are those personal data revealing the ethnic or racial origin of the interested party, their political opinions, religious convictions, union affiliation, genetic data, biometric data, health data and data related to sexual life or sexual orientation of the interested party.
The file manager does not process any data belonging to special categories; however, it is possible that this type of data should temporarily be processed, in which case those who are in a similar situation should inform the Control Body in order to be able to adopt the appropriate security measures.
RIGHTS OF THE INTERESTED PARTY
These are very personal rights that must be exercised by the interested party (providing a photocopy of your ID or other valid documentation, if not done in person) or by a duly accredited representative.
| RIGHT | CONTENTS | CIRCUMSTANCES | TERM |
| INFORMATION | Receiving information on all the circumstances related to processing.[1]. | The data processing will not be possible without having provided the information. | When the data are provided by the interested party: at the time of obtaining the data. |
| When the data are obtained from a third party (vide under “Guiding Principles” the “Information and consent“):
· Within a reasonable time and always within one month of obtaining it. · If they are going to be used to communicate with the interested party, in the first communication at the latest. · If they are going to be communicated to a third party, at the time of the first communication at the latest. |
|||
| COMMUNICATION OF SECURITY BREACH | Be notified of a security breach if it is likely to pose a high risk to your rights and freedoms. | It can be ignored: · When previous security measures were applied that made the data intangible. · When subsequent security measures were applied that made the risk disappears. · When the communication poses a disproportionate effort (then a public communication must be carried out). |
Without undue delay (vide in “Security measures“, the “Registration of security breaches“). |
| ACCESS | Receiving confirmation of whether your data are being processed and, if it is occurring, accessing the circumstances of the processing (vide right of information) and receiving a copy of the personal data subject to processing. | Access can not affect the rights and freedoms of others. | At most, one month from the receipt of the request, which may be extended for another two months if necessary (taking into account the complexity and number of requests).
The extension must be communicated within the first month. |
| PORTABILITY | Receiving the personal data that the interested party delivered in a structured format, which is commonly used and of mechanical reading. | Only in the case that the processing was based on the consent of the interested party and is automated.
The interested party may request that the data be provided to them or to another entity. |
|
| OPOSITION | Opposing to your data being subject to processing. | It can occur when:
-Your personal circumstances so require it: · Although the processing is made in the public interest or the legitimate interest of the data controller or a third party (unless the file manager alleges compelling legitimate reasons). · When the data are processed for research or statistical purposes (unless there are reasons of public interest). -The purpose of the treatment is advertising. |
|
| NOT BE A SUBJECT OF DECISION BASED ONLY ON AUTOMATED PROCESSING (ELABORATION OF PROFILES) | Not being subject of a decision based solely on automated processing, including profiling, producing legal effects on it or affecting it significantly. | It will not apply when:
-It is necessary for entering into or executing a contract. -It is authorized by a European or national regulation. -The interested party explicitly consents to it. |
|
| RECTIFICATION | Rectifying any inaccurate personal data or completing incomplete data. | Each of the recipients to whom the rectified, suppressed or limited information were communicated must be notified. | |
| DELETION (RIGHT TO BE FORGOTTEN) | Supresión de los datos personales. | It will apply when:
-The data are no longer necessary for the purpose pursued. -The interested party withdraws their consent and the processing was based on it. -When the interested party opposes to the processing of their data (vide right of opposition) and other reasons for its processing do not prevail. -The processing was illegal. -The data must be deleted to comply with a legal obligation derived from a European or national regulation. -When the processing was based on the consent of an under-age individual within the framework of the Internet. It will not apply when: -Freedom of expression prevails. -A legal obligation derived from a European or national regulation -For reasons of public interest or research. -The data have to be used for the formulation, exercise or defense against claims. This deletion must be communicated to those entities to which the data were assigned. |
|
| LIMITATION | Limiting the processing only to conservation for the formulation of claims, to protect the rights of another natural person or in the public interest. | It will apply when:
– The interested party challenges the accuracy of the data. -The treatment is illegal and the interested party opposes to the suppression of the same. -The file manager no longer needs the data but the interested party wants to keep them for the formulation of claims. -The interested party opposed to the processing, until verifying that it is viable.If the limitation to the processing is lifted, the interested party must be previously notified.Each of the recipients to whom the rectified, suppressed or limited information were communicated must be notified. |
[1] For more information consult the Control Body.
[2] In the event of a security breach, contact the Control Body.
The interested party, as long as they are able to confirm their identity, can exercise their rights by means of the formalism that they wish.
In the event that the exercise of the right is not addressed by the file manager in a timely manner, the interested party may request protection before the Spanish Data Protection Agency, so all the exercises of rights must be brought to the attention of the Control Body immediately, without any delay.
Only the Control Body is authorized to respond to the exercises of rights.
An individual can request that their data be modified without exercising a right of rectification and this operation can be carried out without the need to notify the Control Body, but if the individual wishing to modify their data expressly notifies that they wish to exercise the right of rectification then the described mechanism must be started.
The blocking of the data never entail their elimination or destruction but they will be blocked in such a way that the access to the data by the personnel that usually had access to them is not possible, such access being restricted only and exclusively in favor of the Control Body in case they must be used under judicial request.
The time span that personal data must remain blocked will depend on each specific case (contractual relationship, legal provision, limitation period of the actions derived from the specific legal relationship, etc.). In case of doubt, please consult the Control Body.
It may also be the case that an interested party requests the withdrawal of a service; this should not be mistaken with the right to the deletion of personal data (right to be forgotten). The withdrawal of a service only implies that this service will no longer be offered; the deletion of the data entails blocking all the data and notifying the deletion to all those to which we assigned them.
THE FILE MANAGER AND THE DATA CONTROLLER
The file manager
The file manager is obliged to apply appropriate technical and organizational measures in order to guarantee and be able to demonstrate that the processing is in accordance with the Law.
These measures will be reviewed periodically by the Control Body.
The controller of the file must maintain, through the Control Body, a record of the processing activities (the files) carried out under their responsibility.
The data controller
When the file manager needs to entrust the processing to a third party (in charge of the processing), they can only choose the one offering sufficient guarantees to apply appropriate technical and organizational measures, so that the processing is in accordance with the data protection regulations in force .
The relationship between the file manager and the data controller must necessarily be governed by articles 28 and 29 of the General Data Protection Regulation.
In the event that the data controller adheres to this document, their relationship with the file manager will be governed by this code of conduct.
OBLIGATIONS OF THE FILE MANAGER AND OF THE PERSONNEL UNDER THEIR AUTHORITY
The processing of personal data
The processing of personal data must be proportional to the purpose pursued, according to the legality of the data (vide under “Guiding Principles“, the “Legality of the data“). If you have any doubts when weighing the proportionality of the processing carried out, please contact the Control Body.
The requirements to measure the proportionality of the data that are being processed will be the following:
- Suitability judgment: Identifying if the processing can achieve the goal pursued.
- Judgment of need: Identifying if the processing is the most moderate one existing to achieve the goal pursued.
- Proportionality judgment: Identifying if the processing is balanced or weighted, that is, if it entails more benefits than damages over the values in conflict.
On the other hand, new files cannot be generated without the authorization of the Control Body, so if you need to create an organized set of personal data with a purpose different to those already established you should consult it beforehand with the Control Body. If the purpose is included within the existing ones, remember that the relevant security measures must be adopted.
Job
Each employee is responsible for their own job and will ensure that no unauthorized person accesses information in their possession. To this end, when employees leave their job they must leave the computer equipment suspended or turned off and make sure that their passwords are always confidential.
Employees will also ensure that no documentation of any kind is left on the printers once their use has been completed.
Duty of secrecy
Anyone processing personal data within the organization responsible for the file is bound by law to professional secrecy regarding them, even if they terminate their relations with the file manager, regardless of whether or not they have signed a confidentiality agreement.
Breaching the duty of professional secrecy is considered a serious infraction.
In the same line, no person other than the one responsible for the file may be given any media that contains personal data to which he/she has had access in the performance of his/her duties without due authorization. If, for the performance of your duties, you should need to provide any media with data to a third party, you must notify the Control Body in advance to authorize the operation.
Communication of data to third parties
The transfer of personal data to a third party unrelated to the file manager without the express, unequivocal and written consent of the interested party is totally prohibited by current regulations. (Vide the exceptions in “Guiding Principles“, the “Consent“).
The Control Body is the only one qualified to manage these authorizations so if for the performance of your duties, you need to transfer personal data to a third party, please consult it.
However, access to personal data by the service providers of the file manager may be allowed, as long as access is essential for the performance of their duties and the file manager has signed an appropriate agreement with them. If you have any doubts about this, consult the Control Body.
International data transfer
If, for the performance of your duties, you need to carry out international transfers of personal data from Spain to another country, please contact the Control Body to determine how you should act.
Electronic resources
You cannot use the resources of the information system to which you have access for private use or for any other purposes than those strictly related to your job, that is, the use made by the file manager of the computer equipment, Internet, corporate email or telephone must be solely and exclusively for the purpose of performing its functions, although the personnel is authorized to use these work tools for personal purposes, provided that it is carried out in a reasonable manner and in good faith. The file manager will be able to control the use of these tools by the staff, being able to monitor the communications or carry out inspections of the equipment. In such cases, it is the obligation of the personnel to facilitate the inspections and the obligation of the company to carry them out complying with all the requirements established by both the legal system and the jurisprudence to the extent possible.
It is very important that you do not install any computer product on your computer at your own initiative in your organization. If, for the performance of your duties, you consider that you need a specific application, please contact Christian Israel Ruiz Pérez, responsible for the technology of the file manager.
SECURITY MEASURES
The data controller and the personnel under their authority will in all cases apply appropriate technical and organizational measures to guarantee a level of security appropriate to the relevant risk.
The persons acting under the authority of the file manager are responsible for the adoption of these measures in relation to their responsibilities, for which we request that you pay special attention to them in order to know your obligations.
In the processing of special data categories, both the specific security measures for this kind of data and the general security measures are included (vide “Principles” for “Processing of special data categories“).
GENERAL SECURITY MEASURES
Safety level evaluation
Risk assessment
The file manager is obliged to verify, evaluate and regularly assess the effectiveness of the technical and organizational measures to ensure the safety of the processing, for which it undertakes to carry out an annual risk assessment of the processing of personal data that will consist of an objective assessment with the purposes of:
- Determining the existing risks for the rights and freedoms of the interested parties.
- Proposing new technical and organizational measures and/or adapting existing ones to mitigate these.
This evaluation will be carried out by the Control Body, which may be assisted by third parties.
When assessing the adequacy of the security level, the consequences of the destruction, any loss or accidental or illegal alteration or communication of, or unauthorized access to processed personal data will be taken into account.
The Control Body undertakes to notify the results of the risk assessment to the administration body and to adopt all the necessary controls to reduce the inherent risk in the processing of personal data, including the renewal of this same document to the extent possible.
In the event that the Spanish Data Protection Agency so requests, the results of the security level assessment will be made available to you.
Impact evaluation
When it is likely that a type of processing (especially if technology is used), due to its nature, scope, context or purposes, involves a considerable risk to the rights and freedoms of those concerned, the file manager will perform, prior to the processing itself, an evaluation on the impact of this processing on the protection of personal data, which will include in all cases the minimum requirements established by law.
In any case, the file manager will proceed to carry out an impact evaluation when carrying out the following processing of personal data:
- Systematic and exhaustive evaluation of personal aspects of the interested parties based on an automated treatment (such as profiling) on the basis of which decisions will be taken that produce legal effects for those interested parties or that may significantly affect them in a similar way.
- Large-scale processing of special categories of data.
- Large-scale systematic observation of a public access area.
This evaluation will be carried out by the Control Body, which may be assisted by third parties.
The file manager undertakes, when appropriate, to obtain the opinion of the interested parties or their representatives in relation to the processing foreseen, provided that it does not prejudice their own public, commercial or security interests.
When the evaluation of the impact results in a high risk of this processing for the rights and freedoms of the interested parties, the file manager undertakes to adopt measures to mitigate it. In the event that the adoption of measures to mitigate the risk does not suppose the disappearance of the high risk, the file manager undertakes to make a prior consultation with the Spanish Data Protection Agency.
If the Spanish Data Protection Agency considers that the processing consulted violates the current data protection regulations and, as a consequence, issues instructions on how to carry out such processing to comply with the regulations, the file manager undertakes to adopt said instructions.
Also, in the event that the Spanish Data Protection Agency orders that the processing is in accordance with current regulations and/or imposes a limitation (both temporary and definitive) of the processing, even if it includes the total prohibition, the file manager undertakes to abide by these instructions.
Pseudonymization or anonymisation
The pseudonymization of the data consists of eliminating or minimizing the risks of reidentification of the anonymized data, maintaining the veracity of the results of the processing in such a way that, in addition to avoiding the identification of the persons, the process of reidentification does not entail a distortion or modification of the data.
In the event that data are to be processed for the purpose of filing in the public interest, for scientific or historical research purposes, statistical purposes or for any other purpose that allows it, the data will be pseudonymized in such a way that no one can access them or, if necessary, only the essential personnel can do it.
If the pseudonymisation is done correctly, the risks of reidentification by unauthorized persons are only residual ones, but never a breach of security measures.
Confidentiality chain
Set of measures aimed at the concealment, masking or disassociation of personal data.
The design of the confidentiality chain should be adapted to each specific situation, and the specific aspects for each block of personal data should be analyzed.
Anonymization process
For each specific case, a concrete anonymization process will be developed, which must be registered and protocolized. The Control Body must necessarily be involved in this protocolization.
Minimization
The minimization of data consists in using exclusively those data that are adequate, pertinent and limited to what is necessary in relation to the purposes pursued.
Vide the principle “Data quality“.
Working outside the premises
Working outside the premises must have been authorized by the Control Body.
If you think that you will need to process personal data outside the premises often, please contact the Control Body to reflect it in the registry.
Temporary files
With temporary files (the data will be processed occasionally and then destroyed), security measures must also be complied with.
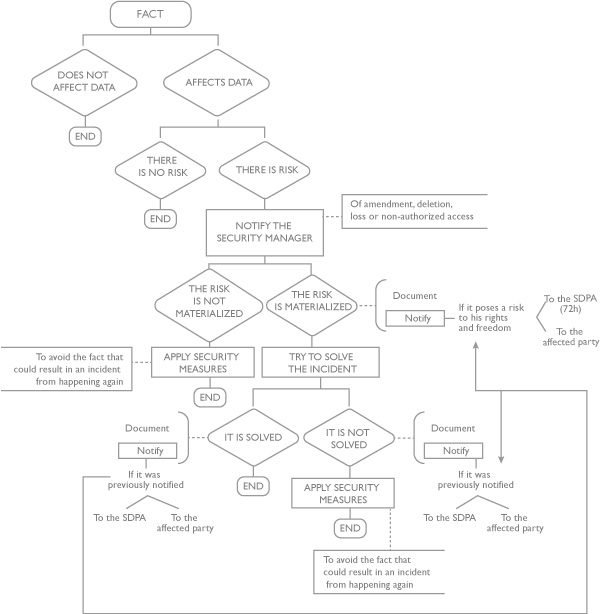
Record of security breaches
There is a procedure for notifying, managing and registering security breaches, so if you are aware of any, please inform the Control Body immediately, especially in the event that the security breach poses a risk to the rights and freedoms of those concerned. In this case the notification of the incident will be urgent.
It is the obligation of the file manager (and, therefore, of its personnel) to immediately notify the Spanish Data Protection Agency of any breach of security that constitutes a risk to the rights and freedoms of natural persons. Therefore, agile communication is fundamental.
The possibilities of security breaches are innumerable and have different levels of seriousness and, therefore, of consequences. It will always correspond to the Control Body to assess the severity of the incident.
The following incidents are provided by way of example: Unauthorized access (or possible access) by someone other than the file manager to the personal data for which it is responsible, unrecoverable loss of personal data, publication of personal data without the consent of the interested party, illicit processing of personal data (such as the most serious incidents that may occur), having to provide the password of our computer to a third party, allowing access by unauthorized personnel to personal data for a specific purpose (e.g., for auditing purposes), providing video surveillance images to security bodies, receiving a complaint regarding data protection (as the most common incidents, but with a possible minor impact).
In case you have any doubts, please, contact the Control Body.
Access control
The file manager must take measures to guarantee that anyone acting under its authority and having access to personal data can only process them following the instructions of that person.
The personnel will only have access to the data they need in order to perform their duties. If you consider that you need access and you do not have it or that, on the contrary, you have access and you do not need it, please bring it to the attention of the Control Body.
Media management
Taking any media outside the premises must be previously authorized.
If you think that you will need to take any media outside the working place on a regular basis, please contact the Control Body.
In the transfer of documentation, all necessary measures will be adopted to avoid the unauthorized processing of data by third parties.
To discard a media, it must be destroyed or completely erased.
According to the DIN 32 757-1 Standard for the Destruction of Documents, the destruction of paper documentation is to be carried out in the following way:
- Level 3 (confidential): documents that can compromise the privacy of people because they contain personal data (non-special categories of data). Particles should not exceed 320 mm² in fragments of 0.9 x 30 – 50 mm or strips of 1.9 mm.
- Level 5 (top secret): documents subject to a high level of confidentiality and extremely high security requirements (special categories of data). The particles should not exceed 10 mm² in particles of 0.78 x 11 mm.
NON-AUTOMATED PROCESSING
File criteria
Archiving must be carried out guaranteeing the correct conservation, location and consultation of the information, so special attention must be paid to this point.
Storage devices
Measures preventing unauthorized access must be used.
Custody of media
When the personnel, in the performance of their duties, should handle documentation outside the place where it is normally filed, they must kept it in such a way as to prevent unauthorized access by third parties.
AUTOMATED PROCESSING
Confidentiality, integrity and resilience of systems
The file manager must guarantee permanent confidentiality, integrity and resilience of the processing systems and services.
Communications networks
When using communication networks, the same measures will be used as for local processing.
Identification and authentication
Only authorized users:
- Will have permission to access automated information, so mechanisms to allow their correct identification must be established. If you detect any incident in this regard, please notify the Control Body immediately.
- Will be able to access the places where the physical equipment supporting the information systems are installed. Whenever they access they must complete the access control (there is a table of records for this reason, were it not available, please request it from the Control Body).
If you believe that you should be authorized to perform your duties but you are not authorized, please contact the Control Body to amend your situation.
If passwords are used:
- These will be strictly confidential (with the exception of the system administrator) and will be modified at least once a year. If a password is to be shared occasionally, a report of difficulties will be issued and it will be modified as soon as possible.
The system administrator will keep passwords strictly confidential.
- Even if computers are shared, each user will have their own password. If you have any doubts about this, please contact the IT manager.
- There must be a system limiting the possibility of repeatedly trying unauthorized access to the information system, so if you notice that you do not have one in your computer, bring it to the attention of the IT manager.
Record of media
All media containing personal data must be properly controlled and inventoried, and under no circumstances may they be removed from the premises without the consent of the Control Body.
To make use of mobile devices owned by the file manager (laptops, USB sticks, hard drives …) previously to them being in your possession they must be inventoried. Therefore, if you have a device that has not yet been inventoried, please let the warehouse manager know.
If you are aware of any media exiting the premises without due authorization you must bring it to the attention of the Control Body.
Personnel cannot use any private media in the performance of their duties, unless expressly authorized.
Backup and recovery copies
Every six months you will verify that the procedure is being carried out correctly. Also, there must be a procedure to recover lost or destroyed data.
POLÍTICA DE MEDIA DESTRUCTION POLICY
Before deleting or destroying any media, make sure that the personal information contained is no longer relevant to the purpose for which it was collected, otherwise it must be safeguarded before its deletion or destruction.
The destruction of media (both paper and electronic) containing personal data may be carried out within the facilities of the file manager, or by a specialized service provider with whom a contract containing the minimum requirements provided by law has been previously signed (if you have any doubts about this, please contact the Control Body). In the latter case the release of the media in favor of the provider must be authorized by the Control Body, who will have to give the file manager a certification proving that the destruction has not only been made but it has been done correctly, and that all legal requirements have been complied with in their entirety.
To dispose a medium that contains personal data, it must be completely destroyed or deleted following the instructions below:
Destruction of paper documentation
The destruction of paper media must be immediate and, according to DIN 32 757-1 Standard for the Destruction of Documents, it is to be carried out in the following way:
- Level 3 (confidential): Documents that can compromise the privacy of people because they contain personal data (non-special categories of data). The particles should not exceed 320 mm² in fragments of 0.9 x 30 – 50 mm or 1.9 mm strips.
- Level 5 (top secret): Documents subject to a high level of confidentiality and extremely high security requirements (special categories of data). The particles should not exceed 10 mm² in particles of 0.78 x 11 mm.
Destruction of electronic media
Before discarding a support it must be completely erased in such a way that it is impossible to retrieve its contents later. After the deletion, please verify that the procedure has indeed been carried out successfully.
If you have any questions, please contact the systems department.
Once the media has been discarded, the media inventory must be updated, so please inform the person responsible thereof. If you have any doubts about this, consult the Control Body.
DUTIES AND OBLIGATIONS OF THE CONTROL BODY
The functions of the Control Body are the following:
- Supervising compliance with data protection regulations.
- Controlling the recording mechanisms.
- Cooperating with the data protection control authority that requests it and, in particular, with the Spanish Data Protection Agency.
- Cooperating with the file manager to promote awareness based on the assumption of the principles of this document and current regulations.
- Answering to the exercises of rights. In this sense:
- The information will be provided to the interested party in a concise, transparent, intelligible and easily accessible manner, with clear and simple language, in writing or by other means, including, where appropriate, by electronic means.
- The interested party may request that the information be provided verbally, but it is not advisable as it can not be demonstrated that it was delivered.
- If there is an objective reason not to respond to an application, the interested party must be informed without delay (at most in a month) of said reasons.
- Informing and advising the file manager and the personnel in charge of processing data within the file manager of their obligations.
- Offering advice to anyone who requests it.
- Reviewing and updating this document on an annual basis and notifying the modifications to all personnel operating under its authority and those who have adhered to the code.
- Evaluating the effectiveness of this document in order to introduce improvements that result in greater effectiveness in the privacy policy adopted.
- Analyzing risk assessments, audit reports and previous impact evaluations and raising their conclusions to the file manager so that it adopts the appropriate corrective measures.
APPLICABLE REGULATIONS
Spanish Constitution
https://www.boe.es/buscar/pdf/1978/BOE-A-1978-31229-consolidado.pdf
Data Protection General Regulation
https://www.boe.es/doue/2016/119/L00001-00088.pdf
Organic Law of Protection of Personal Data
https://www.boe.es/buscar/pdf/1999/BOE-A-1999-23750-consolidado.pdf
Royal Decree approving the Regulation that develops the Organic Law on Data Protection
https://www.boe.es/buscar/pdf/2008/BOE-A-2008-979-consolidado.pdf
18 April 2018